Now, when it comes to FTP servers for Linux systems, there are primarily two big players in the game. One is VSFPD and the other is ProFTPD. These two FTP servers are great, and our next blog on FTP will feature VSFTPD.
This document describes how to install and configure ProFTPD in CentOS 7.0 Server. ProFTPD is an FTP daemon for unix and unix-like operating systems. ProFTPD is developed, released and distributed under the GNU Public License (GPL), which basically establishes it as free software, meaning that it may be sold, licensed and otherwise manipulated in any way desired as long as full and complete source code either accompanies any ProFTPD packages or is made available by any and all sites that distribute pre-compiled binaries. The software can be modified by anyone at anytime, as long as all derived works also are licensed under the GNU Public License.
ProFTPD Version 1.3.5
[root@server1 ~]#
[root@server1 certs]# openssl req -x509 -nodes -newkey rsa:1024 -keyout /etc/pki/tls/certs/proftpd.pem -out /etc/pki/tls/certs/proftpd.pem
Generating a 1024 bit RSA private key
...................................++++++
.........++++++
writing new private key to '/etc/pki/tls/certs/proftpd.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:<--DE
State or Province Name (full name) []:<--Hamburg
Locality Name (eg, city) [Default City]:<--Luneberg
Organization Name (eg, company) [Default Company Ltd]:<--ISPConfig
Organizational Unit Name (eg, section) []:<--Development
Common Name (eg, your name or your server's hostname) []:<--server1.example.com
Email Address []:<--info@example.com
[root@server1 certs]#
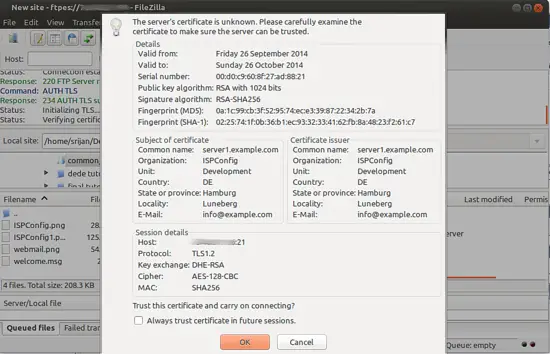
It will ask for trusting the certificates press OK
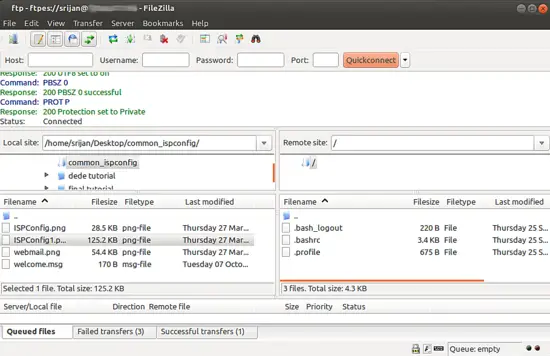
It will be connected to the FTP shared directory with TLS connection.
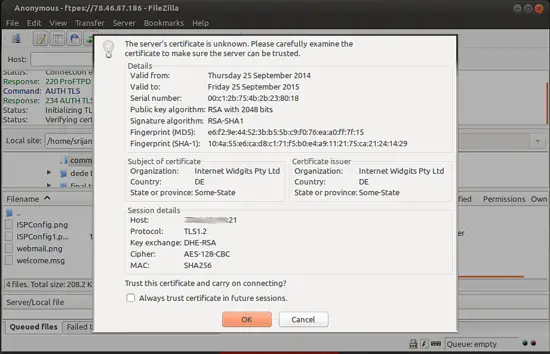
We have successfully connected to the server with Anonymous user.
This document describes how to install and configure ProFTPD in CentOS 7.0 Server. ProFTPD is an FTP daemon for unix and unix-like operating systems. ProFTPD is developed, released and distributed under the GNU Public License (GPL), which basically establishes it as free software, meaning that it may be sold, licensed and otherwise manipulated in any way desired as long as full and complete source code either accompanies any ProFTPD packages or is made available by any and all sites that distribute pre-compiled binaries. The software can be modified by anyone at anytime, as long as all derived works also are licensed under the GNU Public License.
Install ProFTPD
2.1 Installation:
For this enable EPEL as follows:
rpm -ivh http://dl.fedoraproject.org/pub/epel/7/x86_64/e/epel-release-7-2.noarch.rpm
We will first install the ProFTPD and OpenSSL as follows:
yum install -y proftpd openssl proftpd-utils
We need to start the services
systemctl start proftpd.service
systemctl enable proftpd.service
systemctl enable proftpd.service
Addition in CentOS 7.0 we need to configure Firewall-cmd for ftp service as follows:
firewall-cmd --add-service=ftp --permanent
firewall-cmd --reload
firewall-cmd --reload
We can check the ProFTPD version as follows:
proftpd -v
[root@server1 ~]# proftpd -vProFTPD Version 1.3.5
[root@server1 ~]#
2.2 Creating ProFTPD Users
For this I will create a group ftpgroup and user srijan for ProFTPD. I will restrict the user srijan with home directory as /ftpshare
groupadd ftpgroup
Next I will add the user srijan in ftpgroup:
useradd -G ftpgroup srijan -s /sbin/nologin -d /ftpshare
passwd srijan
passwd srijan
[root@server1 ~]# passwd srijan
Changing password for user srijan.
New password: <--ftppassword
Retype new password: <--ftppassword
passwd: all authentication tokens updated successfully.
[root@server1 ~]#
Changing password for user srijan.
New password: <--ftppassword
Retype new password: <--ftppassword
passwd: all authentication tokens updated successfully.
[root@server1 ~]#
Next we need to make the directory protected from removing and renaming its content by any user, so we will change the directory permissions as follows:
chmod -R 1777 /ftpshare/
Now we are ready for ProFTPD connection
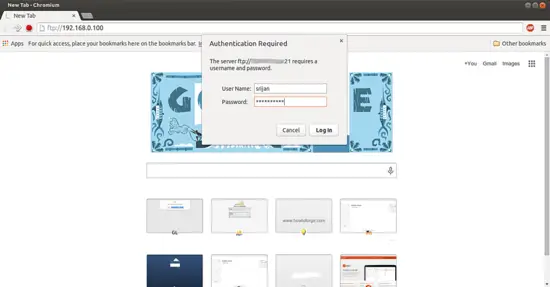
Now we can do login with the user srijan and password at ftp://192.168.0.100


3 Enabling TLS In ProFTPD
In order to enable TLS in ProFTPD, open /etc/proftpd/proftpd.conf before editing the file its better to make the original file backup and then edit the file as shown below:
cp /etc/proftpd.conf /etc/proftpd.conf.bak
nano /etc/proftpd.conf
nano /etc/proftpd.conf
Give the entries as shown
[...]DefaultRoot ~ !adm PassivePorts 6000 6100 [...] #<IfDefine TLS> TLSEngine on TLSRequired on TLSRSACertificateFile /etc/pki/tls/certs/proftpd.pem TLSRSACertificateKeyFile /etc/pki/tls/certs/proftpd.pem TLSCipherSuite ALL:!ADH:!DES TLSOptions NoCertRequest TLSVerifyClient off TLSRenegotiate ctrl 3600 data 512000 required off timeout 300 TLSLog /var/log/proftpd/tls.log # <IfModule mod_tls_shmcache.c> # TLSSessionCache shm:/file=/var/run/proftpd/sesscache # </IfModule> #</IfDefine> [...]
I have added 6000 and 6100 ports for allowing passive mode of ftp, similarily I will allow the passive mode through the CentOS firewalld service as follows:
firewall-cmd --add-port=6000-6100/tcp --permanent
firewall-cmd --reload
firewall-cmd --reload
We can check the ports status as follows:
firewall-cmd --list-ports
[root@server1 ~]# firewall-cmd --list-ports
6000-6100/tcp
[root@server1 ~]#
6000-6100/tcp
[root@server1 ~]#
Additionally we need to tell SELINUX to allow the read/write of the files.
setsebool -P allow_ftpd_full_access=1
In order to use TLS, we must create an SSL certificate. I will create it in /etc/pki/tls/certs, we can generate the SSL certificate as follows:
openssl req -x509 -nodes -newkey rsa:1024 -keyout /etc/pki/tls/certs/proftpd.pem -out /etc/pki/tls/certs/proftpd.pem
Generating a 1024 bit RSA private key
...................................++++++
.........++++++
writing new private key to '/etc/pki/tls/certs/proftpd.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:<--DE
State or Province Name (full name) []:<--Hamburg
Locality Name (eg, city) [Default City]:<--Luneberg
Organization Name (eg, company) [Default Company Ltd]:<--ISPConfig
Organizational Unit Name (eg, section) []:<--Development
Common Name (eg, your name or your server's hostname) []:<--server1.example.com
Email Address []:<--info@example.com
[root@server1 certs]#
Give the above values in red as per your choice, I have just given an example.
Now for security purpose I will make the certificates only readable as follows:
chmod 0440 /etc/pki/tls/certs/proftpd.pem
Finally restart the ProFTPD service as follows:
systemctl restart proftpd.service
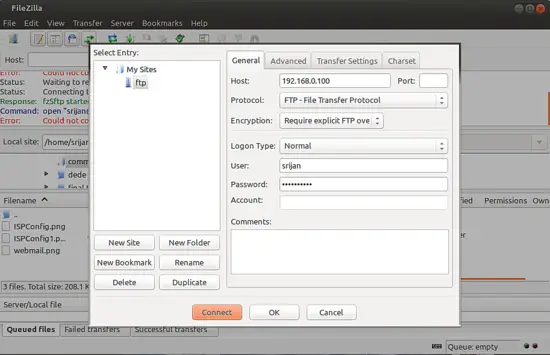
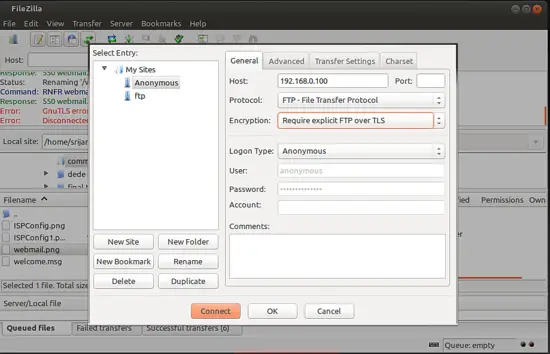
We can connect to the ProFTPD server with Filezilla software, you must have Filezilla installed at client to connect to the server. Open Filezilla and give the details as follows:
Details will be
Host = 192.168.0.100
Protocol = FTP
User = srijan
Port = can be blank if you have not customized it another port than 21
Password = ftppassword (just created above)
Protocol = FTP
User = srijan
Port = can be blank if you have not customized it another port than 21
Password = ftppassword (just created above)
Note: Since we have encryted our connection in above step so we will be using Encryption with Require explicit FTP over TLS
If you have not configured TLS then you can use Use Plain FTP

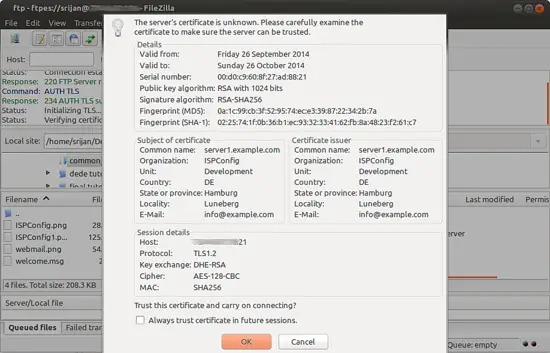
It will ask for trusting the certificates press OK

It will be connected to the FTP shared directory with TLS connection.
4 Anonymous ftp access in ProFTPD
We can make anonymous ftp account in ProFTPD, just add these entries in ProFTPD configuration file:
nano /etc/proftpd.conf
And add these entries at the last of the file,
[...]
###Anonymous share#####
<Anonymous ~ftp>
User ftp
Group ftp
UserAlias anonymous ftp
DirFakeUser on ftp
DirFakeGroup on ftp
MaxClients 10
<Directory *>
<Limit WRITE>
DenyAll
</Limit>
</Directory>
</Anonymous>
Now we need to restart the services:
systemctl restart proftpd.service
Now connect it through Filezilla as follows:

Note: Since we have encryted our connection in above step so we will be using Encryption with Require explicit FTP over TLS
If you have not configured TLS then you can use Use Plain FTP
Press Connect:

It will ask for trusting the certificates press OK

Congratulations! Now we have successfully configured ProFTPD server environment in CentOS 7.0 :)
Comandos de ProFTPd
ProFTPd proporciona varios comandos útiles.
- El comando ftpwho nos permite ver qué usuarios están conectados en un momento dado, qué están haciendo y desde cuándo están conectados:
- El comando ftptop monitoriza ProFTPd en tiempo real:
- Para expulsar a un usuario del servidor FTP, miraremos el ID de su proceso con cualquiera de los dos comandos anteriores (ftpwho o ftptop) y mataremos el proceso. Por ejemplo, para tirar al usuario francis, cuyo ID es 2420, haremos:

Comentarios
Publicar un comentario